Information technology audit checklist
Table of Contents
Table of Contents
An Information Technology Audit Checklist is one of the most important tools for ensuring that a business is running smoothly. Without proper checks and balances in place, a company’s technology systems can be vulnerable to security breaches, data loss, and other critical issues. In this post, we’ll explore the various benefits of an Information Technology Audit Checklist and why it’s essential for businesses of all sizes to implement one.
Pain Points Related to Information Technology Audit Checklist
Most businesses today rely heavily on technology to perform essential functions. Whether it’s managing customer data, financial information, or internal communications, companies without high-quality IT systems are at a significant disadvantage. However, with the increased reliance on technology comes a new set of challenges and risks. Some of the most significant pain points related to information technology include:
- Security risks, such as data breaches, cyber attacks, and theft of confidential information
- System failures, leading to downtime, lost productivity, and missed opportunities
- Compliance violations, which can result in costly fines, legal penalties, and damage to your reputation
- Hardware and software problems, such as outdated systems or incompatible applications
What Is the Target of an Information Technology Audit Checklist?
An Information Technology Audit Checklist helps businesses to identify potential vulnerabilities in their technology systems. By conducting a thorough review of IT processes, infrastructure, and security protocols, companies can make informed decisions about how to improve their operations and minimize risk. The primary target of an IT audit checklist is to ensure that a company’s technology is reliable, secure, and in compliance with all relevant laws and regulations.
Summary of Main Points
In summary, an Information Technology Audit Checklist is an essential tool for ensuring that your company’s technology systems are functioning correctly. By identifying potential risks and vulnerabilities, businesses can take steps to address these issues before they become critical problems. Whether you’re looking to improve security, reduce downtime, or comply with industry regulations, conducting an IT audit is a crucial step in achieving your goals.
Why Use an Information Technology Audit Checklist?
As a small business owner, I know firsthand the importance of maintaining a secure and reliable IT infrastructure. Several years ago, my company experienced a severe data breach that resulted in significant financial loss and damage to our reputation. Since then, I’ve made it a priority to implement best practices for IT security and regularly conduct audits to identify potential issues.
An IT audit checklist is an efficient way to assess the state of your company’s technology systems. By reviewing your infrastructure, applications, and processes, you can identify areas of improvement and take steps to improve security, reduce downtime, and increase overall efficiency. Plus, by staying up-to-date with latest industry trends and regulations, you can ensure that your business is compliant with all relevant laws and regulations.
 One of the significant benefits of using an IT audit checklist is that it helps to prevent problems before they occur. By identifying and addressing potential risks early on, you can avoid costly downtime, data loss, and damage to your reputation. Additionally, implementing best practices for IT security and compliance can help to attract new customers and retain existing ones, who will appreciate the effort you’re putting into protecting their data.
One of the significant benefits of using an IT audit checklist is that it helps to prevent problems before they occur. By identifying and addressing potential risks early on, you can avoid costly downtime, data loss, and damage to your reputation. Additionally, implementing best practices for IT security and compliance can help to attract new customers and retain existing ones, who will appreciate the effort you’re putting into protecting their data.
What Are the Goals of an Information Technology Audit Checklist?
The primary goals of an IT audit checklist are to evaluate your company’s technology systems and identify areas of improvement. This might include:
- Reviewing hardware and software systems to ensure that they meet your business needs and are compatible with your infrastructure
- Checking your security protocols to ensure that they’re up-to-date and in compliance with industry standards
- Reviewing your backup and recovery processes to ensure that you can quickly recover from system failures or data loss
- Assessing your compliance with relevant laws and industry regulations, such as HIPAA, PCI-DSS, and GDPR
 ### How Can You Improve Your IT Audit Checklist Process?
### How Can You Improve Your IT Audit Checklist Process?
One of the best ways to improve your IT audit checklist process is to collaborate with experts who specialize in IT security and compliance. By working with a third-party auditor, you can gain an outside perspective on your technology systems and identify areas of improvement that you might have missed otherwise.
Additionally, keeping up-to-date with industry trends and regulations is critical to ensuring that your IT audit process is effective. By attending conferences, webinars, and professional events, you can stay informed about the latest best practices and techniques for IT security and compliance.
Conclusion of Information Technology Audit Checklist
In conclusion, an Information Technology Audit Checklist is an essential tool for businesses of all sizes. By evaluating your technology systems and identifying areas of improvement, you can increase security, reduce downtime, and improve overall efficiency. Whether you’re looking to comply with industry regulations or stay ahead of the competition, a regular IT audit process is a critical part of achieving your goals.
Question and Answer
Q: What are some of the most common risks associated with IT systems?
A: Some of the most significant risks include security breaches, system failures, and compliance violations.
Q: How often should companies conduct an IT audit?
A: The frequency of audits depends on several factors, such as company size, industry regulations, and the complexity of your technology systems. However, most companies benefit from conducting audits at least once a year.
Q: How can companies stay up-to-date with industry regulations?
A: By working with third-party auditors, attending industry conferences, and participating in webinars and other professional events, companies can stay informed about the latest trends and regulations in IT security and compliance.
Q: What are some key elements of an effective IT audit checklist?
A: An effective IT audit checklist should include a review of hardware and software systems, security protocols, backup and recovery processes, and compliance with relevant laws and industry regulations.
Gallery
Audit Checklist For Information Systems
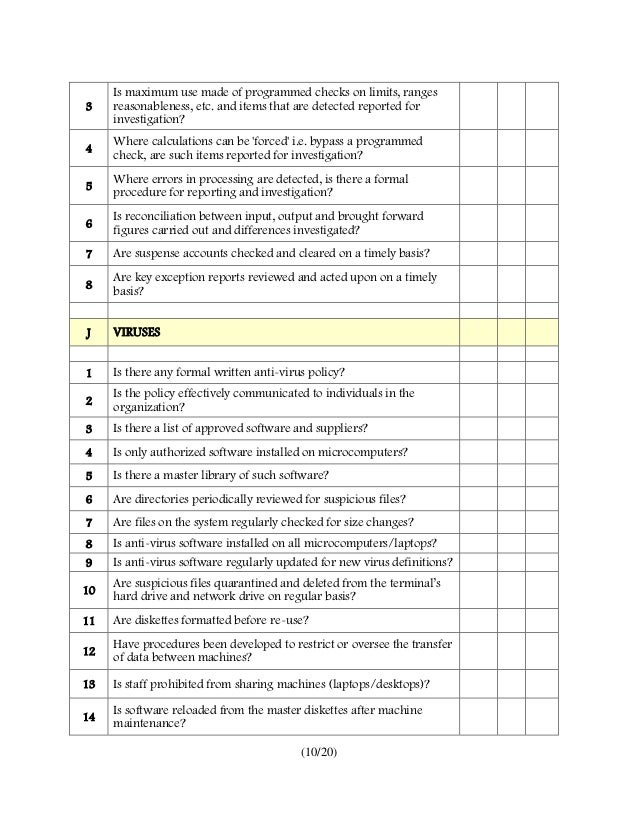
Photo Credit by: bing.com / checklist audit maximum
Information Technology Audit Checklist - Be Structured Technology Group

Photo Credit by: bing.com / audit
Security Audit: Physical Security Audit Checklist Template
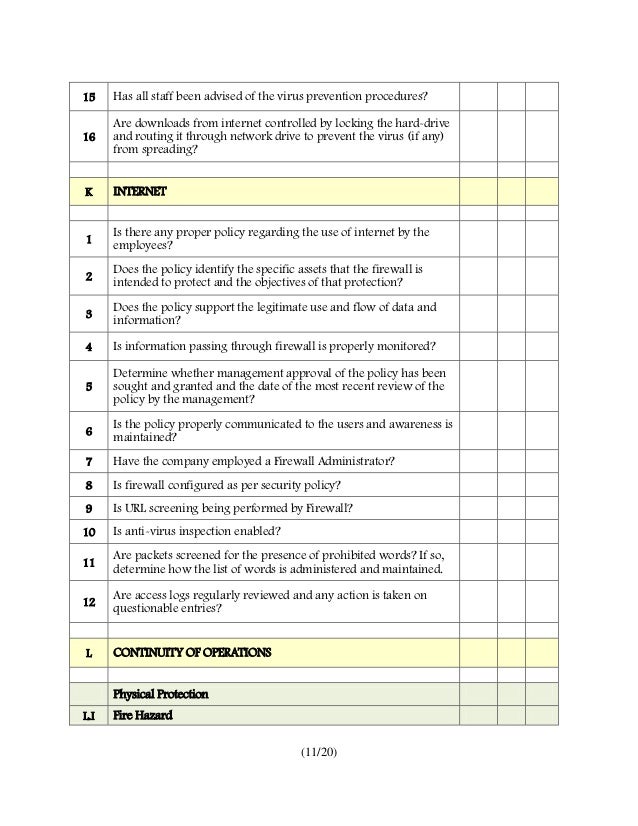
Photo Credit by: bing.com / as9100 questionnaire payroll technology xls guideline employee technologies giac certifications procedural
Audit Checklist For Information Systems

Photo Credit by: bing.com / checklist alarm systems assurance standards retains institute
5s Audit Checklist Excel Purchase Pdf Template For Internal Safety

Photo Credit by: bing.com / bizmanualz compliance regard incident assurance stableshvf intended digitalpictures cumed